Using Tcpdump to Observe Linux Networking
An introduction to one of the most valuable network development tools
Networking is a core functionality of any operating system, including Linux. It enables us to connect with other systems that people are operating and are building on. One of my current projects is building a hyperscaler, and I figure that sharing my knowledge of some of the tools that I am using and will use to implement the networking for the scaler would be valuable for others to read. I want to build up to my scaler’s full functionality by laying the groundwork of the existing systems that I rely on, and it starts with getting basic networking working on Linux and understanding the debugging and troubleshooting tools that I rely on.
This leads up to tcpdump, which is a networking interface monitoring tool. This tool allows us to inspect the traffic that is flowing across networking interfaces on Linux. A networking interface in any operating system is the means by which we can connect our physical machine to the network and operate it at the software, userspace level.
This post is a walkthrough of how we can use Linux networking interfaces and tcpdump to observe the traffic going across our host. For this example, we are going to show different ways to use tcpdump to observe traffic:
The first example is to just dump all the traffic going through our physical NIC. First we need to figure out what our external-facing NIC is, and we do the following:
ip route showWe should see a default entry that looks like the following:
This tells us our NIC for accessing the internet is enp14s0. Next run the following command:
sudo tcpdump -i enp14s0We should see all of our traffic running across the NIC. This is a straight dump of all the traffic and it helps us understand what our network is doing. For the next example, open 2 terminals and run these in separate terminals:
sudo tcpdump -i enp14s0 -n icmpand in another terminal run:
ping 192.168.1.29Go back to your tcpdump terminal and should see traffic that looks like this:
We can run tcpdump and specify a specific protocol like ICMP that we want to capture the traffic on. This makes it really useful for observing and debugging network configurations as ICMP is used for validating and testing network functionality. Finally, run the following:
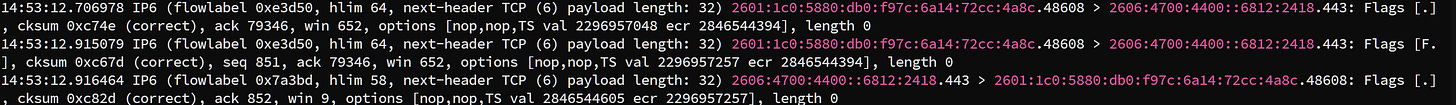
sudo tcpdump -i enp14s0 -n -v port 443and in another terminal run:
curl https://www.thehypervisor.blog > /dev/nullGo to the tcpdump terminal, and you should see something like this:
This shows that we can specify the specific networking port that we want to capture traffic on as well. In this case, we are tracking port 443 because that is the port used for HTTPS traffic, and curl allows us to initiate an HTTPS connection using the network transport protocol: TCP.
In summary, we can use tcpdump for observing and debugging issues at any level of our networking stack, which corresponds to the OSI model. Network software engineers use this tool frequently to verify that their software and networking configurations work properly.